A network protocol is a rule or agreement in a computer network, which is used to control and transmit information between communicating parties during the communication process. Some common network protocols are listed below:
Introduction to TCP/IP protocol
TCP/IP protocol: It is the core protocol of the Internet and is used for data transmission in the network.
TCP/IP protocol is the core protocol of Internet communication, supports the operation of the Internet, and is the foundation of modern network communication.
TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of communication protocols used for data transmission and network communication on the Internet. TCP/IP protocol is the core protocol of the Internet and one of the most commonly used protocols in modern computer networks.
Introduction to HTTP protocol
HTTP protocol (Hypertext Transfer Protocol), used to transfer data between web browsers and web servers.
HTTP (Hypertext Transfer Protocol) is an application layer protocol used to transfer hypermedia documents (such as HTML). It is the basis of Web communication and one of the most widely used protocols on the Internet.
The HTTP protocol adopts the client-server model. The client sends a request to the server, and the server returns a response to the client. An HTTP request consists of three parts: request line, request header, and request body. HTTP response consists of three parts: status line, response headers and response body.
The request line specifies the type of request, the URL requested, and the HTTP version used. The request header contains modification information of the request, such as the browser type, character set, etc. used in the request. The request body contains the data to be sent to the server, such as data from a form.
The status line specifies the HTTP version, status code, and corresponding description information of the response. The response header contains response modification information, such as the character set used in the response, whether to compress it, etc. The response body contains the data returned by the server, such as an HTML document.
The main advantages of the HTTP protocol are simplicity, flexibility, scalability and ease of implementation. It is widely used in web development, mobile application development, API development, etc.
Introduction to SMTP protocol
SMTP protocol: Simple Mail Transfer Protocol, used for the transmission of email.
SMTP (Simple Mail Transfer Protocol) is a standard protocol for email transmission. It defines the interaction process between mail clients and mail servers, and stipulates how mail is delivered between mail servers.
The basic workflow of the SMTP protocol is as follows:

The client connects to port 25 of the mail server through TCP.
The client sends the "HELO" command to the server to indicate its identity.
The server responds with a "220" status code, indicating that it is ready to accept commands.
The client sends the "MAIL FROM" command, indicating the sender's address.
The server replies with a "250" status code, indicating that the command was executed successfully.
The client sends the "RCPT TO" command, indicating the recipient's address.
The server replies with a "250" status code, indicating that the command was executed successfully.
The client sends the "DATA" command to indicate the beginning of the email data.
The client sends data such as email body and attachments.
The client sends the "." command to indicate that the email data transmission is completed.
The server replies with a "250" status code, indicating that the command was executed successfully.
The client sends the "QUIT" command to exit the connection.
The server replies with a "221" status code, indicating that the connection is closed.
The SMTP protocol is a reliable protocol with a timeout retransmission mechanism and error detection mechanism to ensure reliable transmission of emails. The SMTP protocol is commonly used for communication between mail clients and mail servers.
Introduction to POP protocol
POP protocol: Post office protocol, used to receive mail from the mail server.
POP (Post Office Protocol) protocol is the abbreviation of Post Office Protocol and is used to deliver emails between mail clients and mail servers. The POP protocol transmits emails through the TCP/IP protocol stack and is one of the email protocols. The POP protocol allows users to download emails from the mail server to the local computer for reading. The user can choose whether to keep these emails on the server.
There are several versions of the POP protocol, the most commonly used is the POP3 protocol. The basic workflow of the POP3 protocol is as follows:
The mail client connects to the POP3 port on the mail server via TCP/IP (the default port number is 110).
The mail client sends the username and password for authentication.
The mail server verifies the username and password, and if verified, sends the mailing list to the client.
The mail client selects the mail to be downloaded, and then downloads the mail from the server to the local computer.
Once the download is complete, the mail client can choose whether to keep the messages on the server.
It should be noted that the POP protocol can only be used to receive emails, not to send emails. Sending emails requires the use of the SMTP (Simple Mail Transfer Protocol) protocol.
Introduction to IMAP protocol
IMAP protocol: Internet Mail Access Protocol, used for email access.
IMAP (Internet Mail Access Protocol) is the Internet Mail Access Protocol, which is designed to solve the shortcomings of the POP3 protocol in mail management. The IMAP protocol allows users to manage emails on a remote mail server, including reading, deleting, moving, saving, etc. It also supports users to cache emails locally.
The biggest difference between the IMAP protocol and the POP3 protocol is that it not only supports simple email reception and storage, but also supports multiple operations between the client and the server. The basic working principle of the IMAP protocol is as follows:
The client connects to the IMAP server and authenticates.
Clients can view the mail directory and select messages to read.
The header information of the email is downloaded to the client, and the client can choose whether to download the entire email.
The client can mark, move, delete and other operations on emails, and these operations will be reflected on the server.
Clients can save messages to a local cache so that they can be viewed when there is no network connection.
The IMAP protocol has the following advantages over the POP3 protocol:
Multi-device synchronization: IMAP protocol supports multi-device synchronization, and the same email can be viewed and managed on different devices.
Better email management: The IMAP protocol allows users to manage emails on the server, including marking, moving, deleting and other operations.
Mail caching: The IMAP protocol supports saving mails to a local cache so that the mails can be viewed when there is no network connection.
In general, the IMAP protocol is a more flexible and advanced email protocol, suitable for scenarios that require multiple operations on emails and synchronization on multiple devices.
Introduction to FTP protocol
FTP protocol: File transfer protocol, used for file transfer.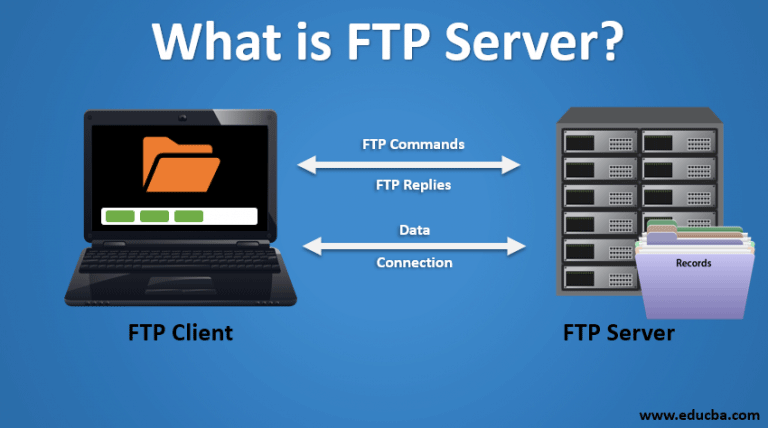
FTP (File Transfer Protocol) protocol is a standard protocol used for file transfer on the network. It uses a client-server model for file transfer, typically using the TCP protocol for connection and data transfer.
The basic functions of the FTP protocol include file upload (send files from client to server) and file download (send files from server to client), as well as some other operations, such as creating directories, deleting files, renaming, etc.
The FTP protocol uses two TCP connections for data transfer, one for control commands and the other for the actual file transfer. By default, control connections use TCP port 21 and data connections use TCP port 20. The FTP protocol also supports two data connection methods: passive mode and active mode.
The FTP protocol is one of the most commonly used file transfer protocols on the Internet and is widely used in file sharing, website management, backup and other fields. Although the FTP protocol is not as secure as SFTP and other protocols, it is still a very practical file transfer protocol.
Introduction to DNS protocol
DNS protocol: Domain name system protocol, used to resolve domain names into IP addresses.![What Is DNS? Types Of DNS Server [Domain Name System] Explain Step By Step](https://3.bp.blogspot.com/-pliAvOUHP7M/XBvKGNPJF1I/AAAAAAAADRc/12h765aA9_MkB2hxKwjDg_-Lk9kxbTQfQCLcBGAs/s1600/What%2BIs%2BDNS%2BTypes%2BOf%2BDNS%2BServer.jpg)
DNS (Domain Name System) protocol is a protocol used to convert domain names into IP addresses. In the Internet, each computer has a unique IP address, but it is easier for people to remember domain names with meaning, such as Ebyte's official website www.ebyte.com. In order to facilitate users to use the Internet, the DNS protocol provides a mechanism to resolve domain names into IP addresses.
When a user enters a domain name in the browser, the browser will first query the local cache to see if there is an IP address corresponding to the domain name. If not, the browser will send the request to the local DNS server. If the local DNS server does not know the IP address of the domain name, it will send a query request to the root domain name server. The root domain name server will return the IP address of the top-level domain name server corresponding to the domain name, and the local DNS server will then send a query request to the top-level domain name server. This recursive query continues until the local DNS server finds the IP address of the domain name and returns it to the user.
The DNS protocol uses UDP protocol for communication and uses port 53. During the communication process, domain name query messages and domain name response messages are used for data transmission. The domain name query message contains information such as query type, query category, and query domain name, while the domain name response message contains resource records, authorization information, and additional information.
The DNS protocol plays a very important role in the Internet. Almost all Internet applications require domain name resolution through the DNS protocol.
Introduction to DHCP protocol
DHCP protocol: Dynamic Host Configuration Protocol, used to automatically configure IP addresses in the network.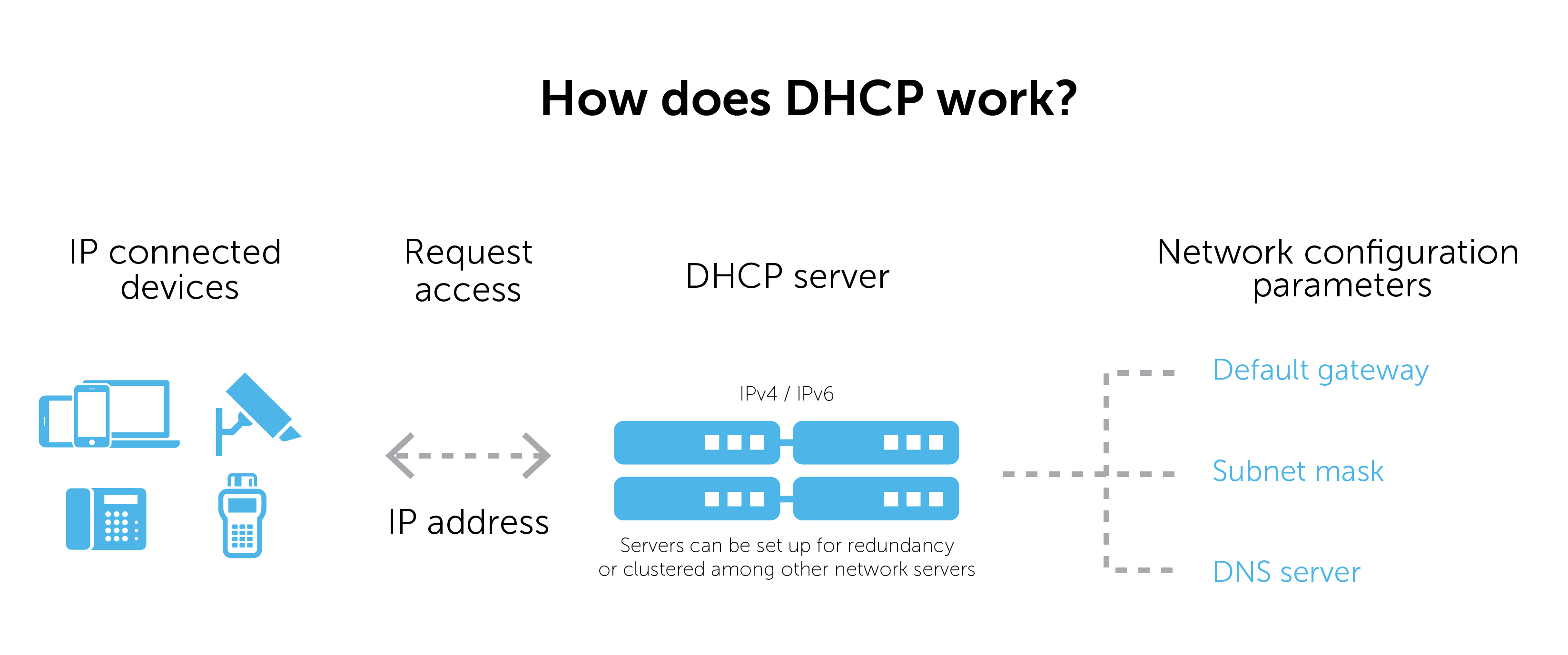
DHCP (Dynamic Host Configuration Protocol) is a network protocol within a local area network. It is mainly used to automatically assign IP addresses and other network parameters, such as subnet masks, default gateways, DNS servers, etc.
The DHCP server maintains an address pool in the LAN. When a client (such as a computer, mobile phone, etc.) requests an IP address, it communicates with the DHCP server through the DHCP protocol. The DHCP server allocates an available IP to the client from the address pool. The address is returned to the client in the network parameters through which the client can connect to the network.
The advantage of the DHCP protocol is that it can easily manage IP addresses, reduce the workload of manually configuring IP addresses, and avoid IP address conflicts. The DHCP protocol can be used in local area network environments such as home networks and enterprise networks.
Introduction to SNMP protocol
SNMP protocol: Simple Network Management Protocol, used for the management and monitoring of network devices.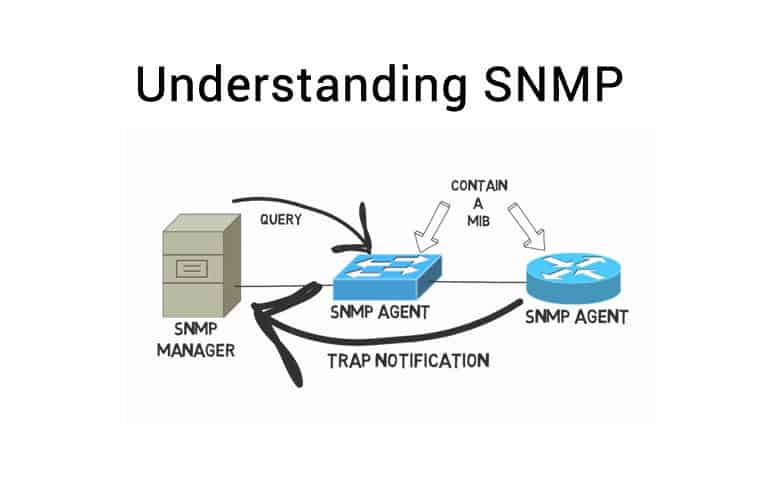
SNMP (Simple Network Management Protocol) is a network management protocol used to manage and monitor network devices. It allows network administrators to monitor devices on the network, collect information and configure the devices.
The SNMP protocol consists of two parts: the management system and the managed system. A management system can be a software program or a hardware device that manages devices on a network. The managed system refers to network equipment, such as routers, switches, servers, etc. These managed devices have an SNMP agent that can respond to requests from the management system.
SNMP uses a simple, text-based protocol, usually running on top of the UDP protocol. Its core concept is the Management Information Base (MIB), which contains device configuration and status information. MIB is a tree structure composed of a hierarchical object identifier (OID). Each OID represents specific information of a device, such as CPU utilization, memory usage, etc.
SNMP is primarily used for network management, allowing administrators to monitor devices, collect information, and configure devices. It can be used to monitor network performance, discover and troubleshoot devices on the network, and more. Due to its simplicity and scalability, SNMP is widely used in various network devices and management systems.
Introduction to SSH protocol
SSH protocol: Secure Shell protocol, used to remotely control and manage computers.
SSH (Secure Shell) is a secure network protocol used to securely transmit data over insecure networks. It uses encryption technology to protect all transmitted data, including authentication credentials and transferred commands, files, and data.
The SSH protocol allows users to connect to remote computers or devices over the Internet or other unreliable networks and execute commands or transfer files in a secure manner. SSH provides higher security and privacy protection compared to other transfer protocols.
The main uses of SSH are to provide secure remote login between computers and network devices, and to transfer files between computers and network devices. It can also be used to securely transfer other types of data, such as emails and databases.
There are multiple versions of the SSH protocol, including SSH1, SSH2, and SSH3. SSH2 is the most commonly used version and offers better security and functionality. SSH3 is the latest version, which adds some new features and security based on SSH2.
Introduction to Telnet protocol
Telnet protocol: Remote terminal protocol, used to log in and control computers remotely.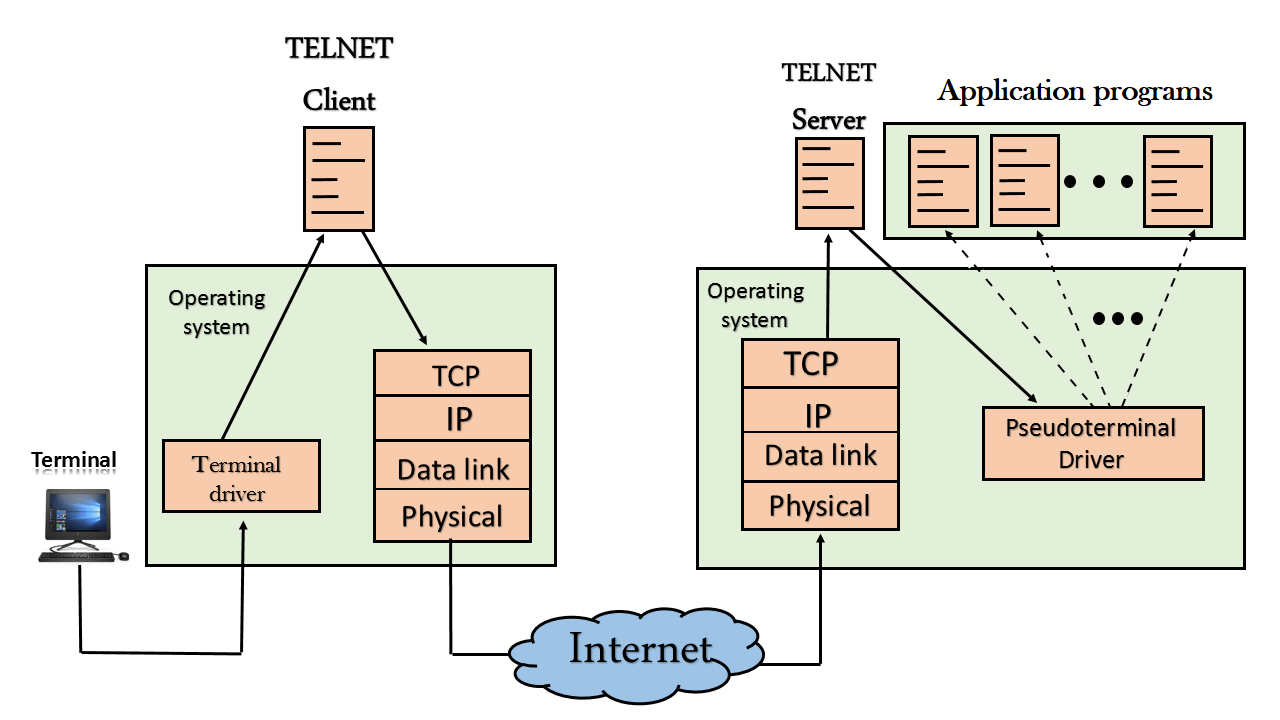
Telnet (Terminal Network) is a remote login protocol that allows users to remotely log in to a remote host and execute commands through the Internet or a local network. Through Telnet, users can use a terminal emulator on their own computer to log in to a remote host and execute commands as if they were on the local computer.
The Telnet protocol works by establishing a virtual terminal connection between the client and the server. The client controls applications on the server by sending commands and characters. It usually communicates using the TCP protocol and uses port 23. Once the connection is established, the client can interact with the remote host through a Telnet session.
The main advantage of the Telnet protocol is that it allows users to execute commands on the local computer on the remote computer, which makes it more convenient to manage and maintain remote computers. However, since the Telnet protocol is not encrypted during transmission, it presents a security risk. Now, the more secure SSH protocol has become the preferred protocol for remote login.
Introduction to SIP protocol
SIP protocol: Session Initiation Protocol, used for real-time communications and voice and video calls.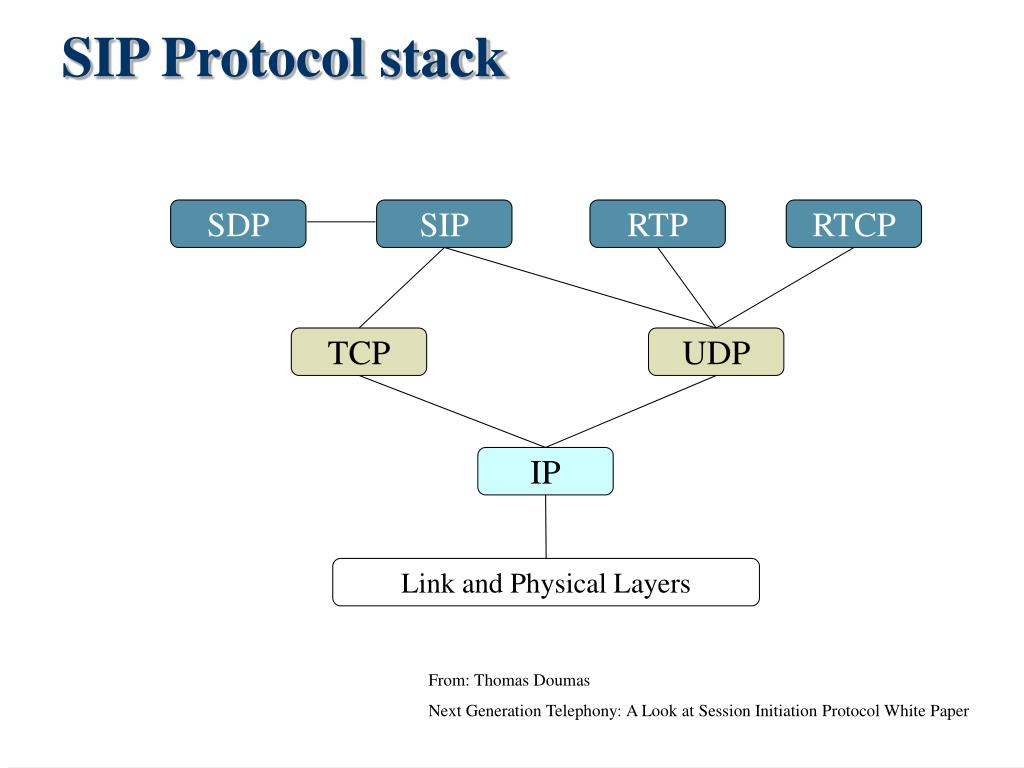
SIP (Session Initiation Protocol) is a communication protocol used to control multimedia sessions. It is commonly used in multimedia communication applications such as Internet telephony, video conferencing, and instant messaging.
The SIP protocol controls media communication between two or more terminals by establishing and releasing connections on the network. It allows users to communicate with others from anywhere on any device, regardless of location or device. At the same time, SIP can also provide a variety of media services, including voice, video, chat, file transfer, etc.
The core of the SIP protocol is "session", which is the process of establishing and maintaining communication connections. It defines how to establish, maintain and close sessions, and how to transmit multimedia data. The SIP protocol uses text-formatted messages for communication, which makes it easier to expand and adapt to different network environments.
The SIP protocol can be used in conjunction with other protocols, such as RTP (Real-time Transport Protocol) for transmitting multimedia data, and SDP (Session Description Protocol) for describing the parameters of a media session.
In short, the SIP protocol is an important multimedia communication protocol, which provides users with a more flexible, convenient and efficient communication method.
Introduction to SSL/TLS protocol
SSL/TLS protocol: Secure Sockets Layer/Transport Layer Security protocol, used for encryption and identity authentication of network connections.
SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocol is a secure transmission protocol used to encrypt and authenticate data on network connections. Its main purpose is to protect the privacy and integrity of network communications.
The SSL protocol was originally introduced by Netscape in 1994. Later, due to its popularity and application, it became a standard protocol under the IETF (Internet Engineering Task Force) organization, that is, the TLS protocol. Its goal is to replace the SSL protocol.
The SSL/TLS protocol is built on the TCP protocol and protects data by using certificates and encryption algorithms. When establishing a connection, communication between the server and client goes through a handshake process that negotiates encryption algorithms, creates a secure channel, and authenticates. During the data transmission process, the SSL/TLS protocol encrypts the data to prevent data from being tampered with or eavesdropped.
The SSL/TLS protocol is widely used in various network applications such as Web, email, and instant messaging, ensuring the security and privacy of network communications.
Introduction to ICMP protocol
ICMP protocol: Internet Control Message Protocol, used to transmit error information and network status information in the network.
ICMP (Internet Control Message Protocol) is a network protocol mainly used to transmit control messages on IP networks. ICMP messages are transmitted in IP datagrams and are usually used to test and diagnose network problems. For example, the Ping command uses the ICMP protocol.
ICMP messages are usually used in the following areas:
Ping test: Ping is a network diagnostic tool based on the ICMP protocol. It is mainly used to test network connectivity and latency. You can determine whether the target host is reachable by sending an ICMP Echo Request message to the target host and waiting for it to return an Echo Reply message. .
Router failure detection: ICMP messages can also be used to detect router failures. When the router cannot reach the destination host, it will return an ICMP Destination Unreachable message to the source host.
TTL (Time to Live): TTL is a field in IP datagrams that is used to limit the number of transmissions of datagrams in the network to prevent datagrams from circulating in the network without limit. When the TTL reaches 0, an ICMP Time Exceeded message is returned to the source host.
In short, the ICMP protocol is a very important network protocol that can be used to test and diagnose network problems and ensure the normal operation of the network.
